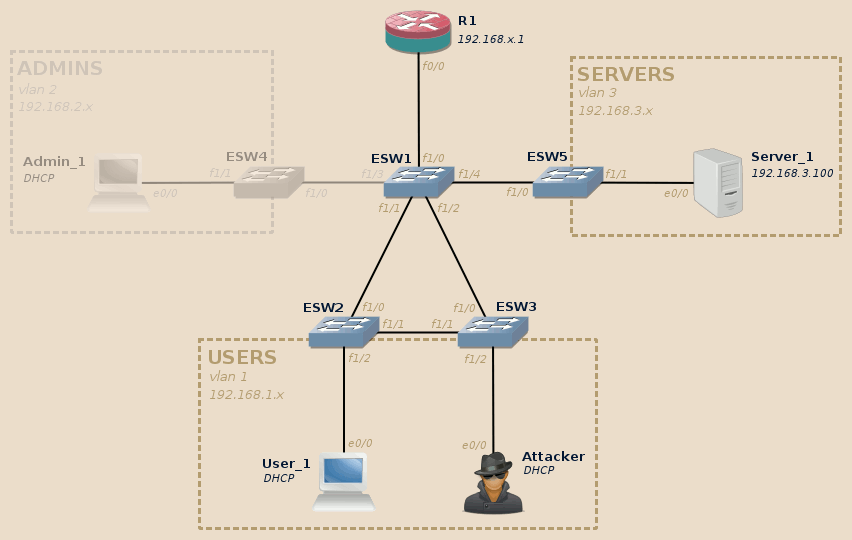
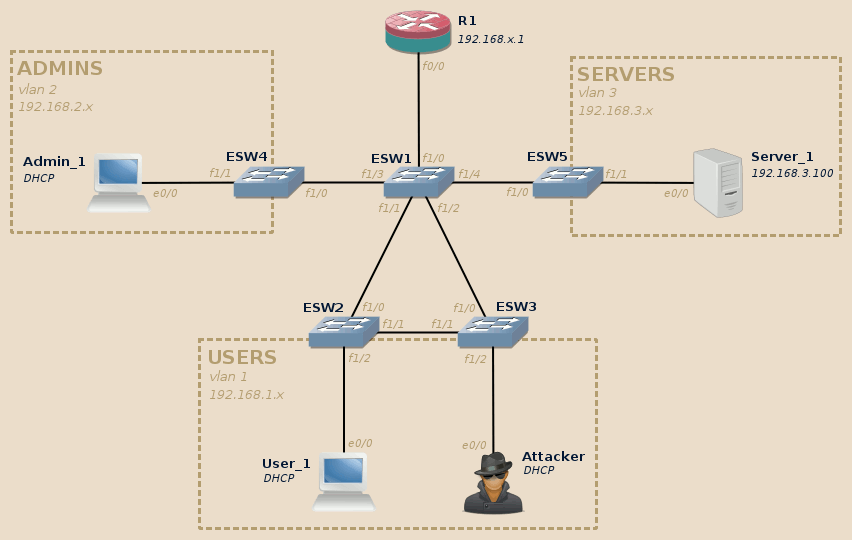
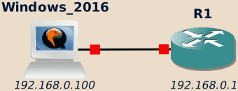
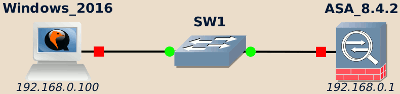
DHCP allows devices to automatically get their network configuration when bringing up a network interface (typically when booting).
This configuration usually includes, among other thing, the IP address attributed to the device, the DNS domain name and the IP address of the default router, of the DNS server and of the NetBIOS name server.
This configuration, is allocated to the device only for a given time: the lease time. Lease time may vary largely depending on the environment requirements. It is typical to find values ranging from a few dozen of minutes to a few weeks. When half of the lease time expired, the device starts to try get in touch with the DHCP server to renew the lease.
Clients initially asking for the attribution of an IP address start by broadcasting a DHCP DISCOVER message.
A typical DHCP exchange is as follow:
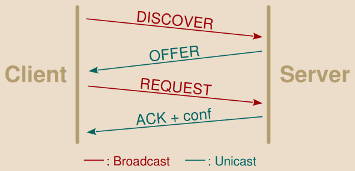
-
DISCOVER: The client without IP address configured …