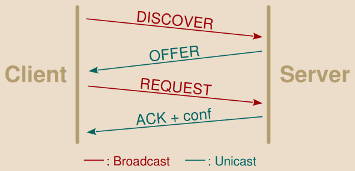
Web shells are backdoors relying on server-side scripting languages to be executed by the targeted server and usually accessed through a browser. While focused on wwwolf’s PHP webshell features, some part of this post are general and can be applied to other other webshells as well.
While some web shells attempt to provide the most complete post-exploitation frameworkas possible, and are therefore heavy and prone to bugs and incompatibilities, wwwolf’s PHP webshell considers the web shell as a transitional step in taking over a server.
wwwolf’s PHP webshell focuses on the functionalities necessary to do:
- Local enumeration to discover the target’s environment and choose your next step.
- Payloads and toolkits files transfer and execution, to proceed with your next step.
It tries its best to:
- Be unobtrusive, with a simple yet efficient interface.
- Be reliable, being as tolerant as possible regarding the target’s environment and …