In this article:
Security professionals often recommend to use a dedicated password manager software, such as KeePass1, which allows to easily prevent password reuse while ensuring a safe storage of the passwords.
Did I just say… “easily”? For the wide public, this “easiness” may not be so obvious. The fact alone to have to install, learn and use a new software just to store the password which allows to access the website which, in turn, allows you to do your things: end-users often consider this over-killing…
And they may be right.
Their usual reaction is therefore either to rely on a single “well thought and complex password” to secure their whole digital life, or build an over-engineered mental algorithm to create unique (but easily guessable, even when they don’t think so) passwords, loosing data because of a forgotten password or being stuck because they are currently at their office while their password is written on a paper stored in drawer at their home.
There is however a good alternative which, after a few easy steps, can provide a well-balanced solution between security and usability for casual users.
Password managers limitations
Power users and technical people have a very different use of the computer than what I may call the “common folk”. They use various software: SSH here, remote desktop there, file transfers software and command-lines, thick clients, administrative interfaces, encrypted files and data: all this compose their daily bread.
In this case, adding one supplementary software centralizing credential management in one safe place has indeed only advantages, both in terms of security and usability. But this is not the way the wide public use their computer, nor the way they use the interweb.
Moreover, the practical security gain added by using a standalone password manager may not be the one expected.
In fact, if the password manager is used as is, using an encrypted database stored in the user’s files and relying on a password to decrypt it, the practical security gain compared to using the browser’s built-in password manager will be very marginal:
-
To have access to your browser’s password manager, an attacker needs to have access to the user’s file. He will therefore have access to the standalone password manager database as well.
-
Having access to the users files, the attacker will most likely also have the possibility to install a key logger or any other malicious software. It will work mostly the same way no matter the location and the way you store your passwords.
Note that I’m not implying that standalone password managers are useless, far be it from me!
Standalone password managers allow:
-
To centralize the credentials required for various software, when your browser is not the only one asking you for a password on your machine. In this case it is more a convenience software than a real security tool.
-
To use other, more advanced authentication forms than a password to unlock the passwords database, potentially combining several complementary authentication systems together.
-
To isolate the software storing the password from the software using it, we will come back on this when we will deal with sandboxingat the end of this article.
I may forget some other specific use-cases, but the idea remain that using a password manager software just for the sake of using one won’t make you more secure. You might as well use your browser’s native password manager and gain in usability.
While security might sometimes impact usability, impacting usability doesn’t necessarily improve security. The easiest solutions may also be the safest ones.
What about all-in-one password manager add-ons?
Several add-on propose all-in-one solutions for password storage in Firefox.
Often, these add-ons either reinvent the wheel by storing the password in local file, or more often your credentials are sent to machines controlled by the plugin author (so called “cloud-based” password managers).
Developing and maintaining an add-on costs money and effort, developing and maintaining a cloud infrastructure costs even more.
In these cases, you have to ask yourself:
-
Who is/are the author(s) of the add-on?
-
What is their benefit? Especially if a company is involved there must be a benefit somewhere. In this case remember that if you did not pay for something, it means that you are the product, and that the company somehow manages to produce money from the data you provide it.
-
What happens if the project is deemed not profitable and abandoned, will you loose all your passwords? Such situations also happens when, on the contrary, the project becomes too profitable and the company gets bought by another one deciding to close the current service.
-
What happens if the author unilaterally decides from one day to another to dramatically change the plugin behavior, adding useless and complex features, making it invasive, in other words turning it into what you may perceive as crap?
-
Can you trust the author and his add-on? Is it widely used? Has it been checked for vulnerabilities? Did it encountered security issues by the past, and if yes how were they handled?
In this article we will rely on vanilla Firefox for the main tasks, with a few small add-ons adding simple features so it shouldn’t be hard to find a replacement if needed.
Warning
Some add-on offer a storage-less password solution.
They rely on the website URL and a master key provided by the user to generate a hash acting as a unique password. The security of this system is comparable to sharing your whole passwords database which each website.
Indeed, if an attacker manages to get his hands on one of your hashes, he can try to brute-force it to try to obtain your master password (given that most of these add-on never went through the hands of experienced cryptographers, most chances are that such brute-force attack will be very quick). Once the attacker got the master password, the game is over as he virtually obtained all your passwords.
As a safety measure, passwords for different websites must therefore be not only different, but also unrelated to avoid such weakness. There is no other way to achieve this than generating a random password for each website and storing a list of generated passwords somewhere.
Choosing a new password
While Firefox provides a password storage functionality allowing a user to store a unique password for each account and service, it doesn’t help the user to choose a good password in any way, resulting in users often choosing weaker passwords due to various bias.
Moreover, from a functional point-of-view, there is just no point in manually choosing a password that you won’t need to remember at all.
Note
Human are bad in creating random strings.
Factors such as the key location on the keyboard or characters frequency in the users’ language often influence users toward the same subset of characters. Good password cracking software rely on such bias when brute-forcing a password.
It is expected that letting a software choose a password for you may produce an odd feeling. This is actually the most secure way to operate.
Encryption keys used to secure higher security environment are software generated. There is not reason why software would not also be used to generate more basic credential such as passwords.
The only requirement is to rely on widely used software to limit the chances of a bug in the software resulting in another bias. For this reason you want to avoid using software found on random forums and used by two or three people for security purposes.
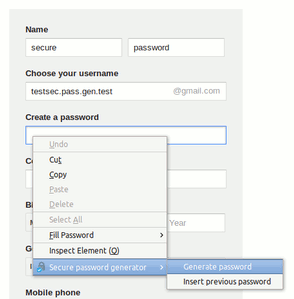
The Firefox add-on page offers several password generation tools such as Secure Password Generator. Such software allows to easily generate new and safe passwords in just a click without having to think about it.
If you need to access previously generated passwords, you can access them in the Security section of Firefox’s Options screen.
Filling login forms
This is a thing I just don’t understand in Firefox password manager implementation: why in the hell does it want to automatically pre-fill authentication forms?
The so-called “sweep attack” takes advantage of this behavior to steal users passwords by automatically, successively and quickly simulating the login pages of various websites, letting the browser automatically fill the fields and then retrieving the values filled by the benevolent browser without the user even noticing.
Note
This attack usually relies on malicious WiFi access points (sometimes automatically selected as “known access point” without requiring user consent), but are not limited to them as ISP-provided Internet routers are now more and more targeted by malicious software and can be used to achieve similar attacks.
The proprietary browser Opera, which often comes with innovative ideas for web browsing, requires a manual intervention to fill authentication forms. This is the only sane things to do and effectively prevents such attack.
There are a some modules which attempt to port this functionality to Firefox, but as long as you just need to protect yourself against this attack without any additional bell and whistles Firefox already natively proposes good a solution. This solution, however, is not used by default to not “annoy and alienate all the users who expect autofill to work as it has since Firefox 1.0” (source) and Firefox went this far as to even hide this functionality from the standard options screen (don’t ask me why, such decisions dumbing users down just completely boggles my mind), even-though websites such as MozillaZine recommend to take advantage of it.
To disable the automatic filling of authentication forms:
- In Firefox URL bar, type
about:config. - You should get a warning message, click to continue.
- In the search bar, type
signon.autofillForms. - The default value for this parameter is
true, double-click on it to change its value tofalse.
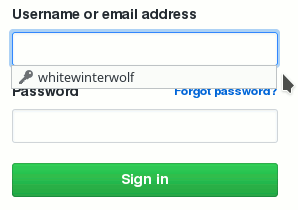
From now on, Firefox won’t automatically fill any login form. Simply click on the login field, and you will get a dropdown menu allowing to select the account to use:
Keeping the password database available
When using a database to store all your passwords, you must take specific measures to ensure its availability:
-
Of course when you’re on the go, so you can access your account from home, work, mobile devices, etc.
-
But also in case of a disaster: you don’t want to loose your passwords the day your hard-disk will break.
Firefox natively provides Firefox Sync, a remote repository used to synchronize the Firefox data, including its password database. This service has been built with privacy in mind. The data being encrypted client-side, Mozilla teams cannot access its content (Mozilla interest here being to get more Firefox users).
Note
As with any cloud storage service, Firefox Sync requires some degree of trust between the service provider and you.
As such, Firefox Sync requires you to trust Firefox developers. This, however, should already be the case if you are already using their browser. Moreover, Mozilla, the foundation behind the Firefox browser, is usually well regarded by freedom advocates such as the EFF and worked with them on several freedom and privacy-related projects.
Moreover, for advanced use-cases, Firefox Sync is an open-source technology and it is possible for you to setup your own Firefox Sync server, thus preventing even your encrypted data from leaving your control at any point
Warning
If you plan to sync personal and professional devices, pay attention at what you are syncing.
In particular, if NSFW websites appear in your personal browsing history and you are syncing the browsing history with professional devices, these entries will also appear in the browsing history of the professional devices and your employer may take you liable about that.
Firefox Sync allows you to select what data you want to sync. You can perfectly use it to sync only the password and not the rest.
Warning
Using Firefox Sync does not exempt you from doing proper backups.
Better be safe than sorry!
Local storage
By default local storage is not protected: password are stored locally as if they were written in a plain text file.
This, however, does not mean that you necessarily need more or that this makes you insecure. A security system is only valid as long as it provides an effective protection against a given threat. There is no point in encrypting a file if an attacker having access to the file would also have access to your password.
Encryption can be enabled at several location, and we will see that encryption is not necessarily the only nor necessarily the best way if you want an additional layer of protection around your passwords.
Full disk encryption
I’m a proponent of full disk encryption and prefer to enable it whenever possible.
Full disk encryption encrypts most of the hard disk content (encryption at the partition level). Usually the bare minimum remains clear to be able to ask the boot password to the user and allow to initiate the booting sequence.
This protects not only your password database, but all your data from various threats:
-
When a device is stolen you can be confident that its content will not be readable.
-
When disposing of a old or broken hard disk you can be confident that no one will ever be able to recover any of its content.
-
When handing your device to a stranger (at a repair-shop for instance) you can be confident that your data will remain protected from prying eyes.
Full disk encryption however only protects the data of turned off devices. It does nothing to protect your data while the device is running.
Note
For mobile devices, some applications exist to turn off or reboot the device after a certain number of unsuccessful attempts to unlock it.
Such applications allow to automatically retreat behind the stronger full disk encryption protection when there is a suspicion that the running device has been stolen.
File level encryption
As an alternative to full disk encryption, some operating system offer file level encryption.
In this case, the encryption protects only the content of the files below the user’s home directory. File decryption occurs transparently with the password used by the user to open a session.
Warning
Depending on the system used, only file content may be protected. File names, sizes and directories structure may remain accessible in clear form.
This protection is weaker that full disk encryption, but is mainly used to protect files from prying eyes in the case of multi-users environments.
This features protects the files as long as the user has no opened session on the machine. As soon as the user opens a session any process can potentially access any of the user’s files.
Firefox password database encryption
Firefox allows to use a master password to add an additional protection layer for your web credentials.
The protection added by this feature, even when using reasonable passwords, is comparable to a small padlock: enough to keep your password out of prying eyes but can usually be defeated in a very short time by an attacker.
Note
Firefox master password acts as a local storage password.
If combined with Sync, it will be used to wrap both the synchronized websites credentials and Sync credentials itself in a container encrypted using the master password2. The master password itself will not be synced among devices but remain local.
Different devices can therefore use Sync using different master passwords or master passwords can be used only on certain devices and not others.
For instance, you can use Sync without a master password on you home computer, and Sync with a master password on your company computer, accessible by network administrators, to somewhat “mark” your passwords database as private data.
The encryption implemented by Firefox is far from being the worst among common browsers3 and still remains hard to brute-force when long passphrases are being used. There is an open ticket on Mozilla bug tracking system asking for improvement of the encryption used which would allow to get good resistance against brute-forcing even for common size passwords.
While not totally inactive, this ticket doesn’t show much progress most probably as, would an attacker gain access to your Firefox files, there are dozens of ways he could use to get access to your passwords (this is the reason why Google always refused to implement any equivalent functionality in Chrome). So, would the strongest algorithms in the world be used, from a practical perspective the overall security of the Firefox password manager would still be equivalent to a small padlock.
Nevertheless, small padlock still have their use, as does Firefox password manager.
Warning
Firefox password manager does not encrypt the cookies.
If you’re planning to use Firefox master password featue, you will most likely want to set Firefox to delete all cookies upon exit to ensure (in Options > Privacy, under the History session select Use custom settings for history, then set Keep until to I close Firefox).
Applications sandboxing
If you really want to protect Firefox passwords from being accessed by other processes, instead of encrypting some Firefox files with a password that an attacker would capture anyway you must simply prevent these other processes from accessing any Firefox files.
This is achieved through software sandboxing which allows to isolate potentially untrusted applications from the rest of your system.
Common sandboxing software include:
- For Windows environments: Sandboxie.
- For Linux environments: Firejail4.
- Specific Linux distributions also exist such as Qubes OS and Subgraph OS which provide software isolation services at their core.
Simply running Firefox in a sandbox won’t help to protect your Firefox password manager database!
The idea here would be instead to run the other applications (in particular every other application communicating over the network) in sandboxes to prevent them from accessing Firefox files (Firefox itself can be sandboxed to prevent any malicious code running on web page to access your private documents or other application files).
Moreover, if you find yourself needing such product, most chances are that you will be better off using a dedicated password manager software. This will allow you to implement a stronger isolation between the password management and the browsing functionality.
Summary
Here is my recommended way to get a reasonably secure and easy to use password storage using Firefox built-in password manager, suitable for casual users:
-
Use Secure Password Generator to generate new passwords (when creating an account or replacing an old password).
-
From the
about:configpage, setsignon.autofillFormstofalseto require a human intervention to fill a login form. -
Use Firefox Sync to share your passwords database between several devices.
And from a more general perspective:
-
Use full disk encryption whenever possible to prevent the content of your computer and devices to fall into the wrong hands.
-
Backup you data to prevent the loss of you computer and devices content.
-
Don’t confuse the free, open-source and well known KeePass with the unrelated, closed-source and paid KeyPass software. ↩
-
With the advent of Sync 1.5, Mozilla developers seemingly initiated a movement to push the master password feature away, putting Sync credential out of its scope and making Sync and master password incompatible. This created a lot of reactions among the Firefox users community, mostly tracked in bug #995268. This thread being quite long the most relevant comments I noted were: #37, #38, #48, #49, #67 and #58. ↩
-
RaiderSec published a comparative study on passwords protection among common browsers, and even in its current shape Firefox manage to keep the head up. For the French readers, the MISC magazine also published a very insightful analysis on Firefox password manager encryption.
Moreover there is an urban legend stating that enabling Firefox FIPS mode allows to benefit from a better encryption. This is bullshit, at best this enforces a minimum strength for the user’s master password but the encryption used remains the same. In fact it seems that the FIPS mode has no concrete use-case in Firefox and is on its way to be pushed away. ↩ -
Firejail is named after the network firewalls, it is not a Firefox plugin nor is limited to Firefox! ↩